Reverse Engineering Stuxnet — The First Industrial Cyber Weapon
When Code Becomes a Weapon: What Stuxnet Revealed — and Why You Can’t Ignore It Today
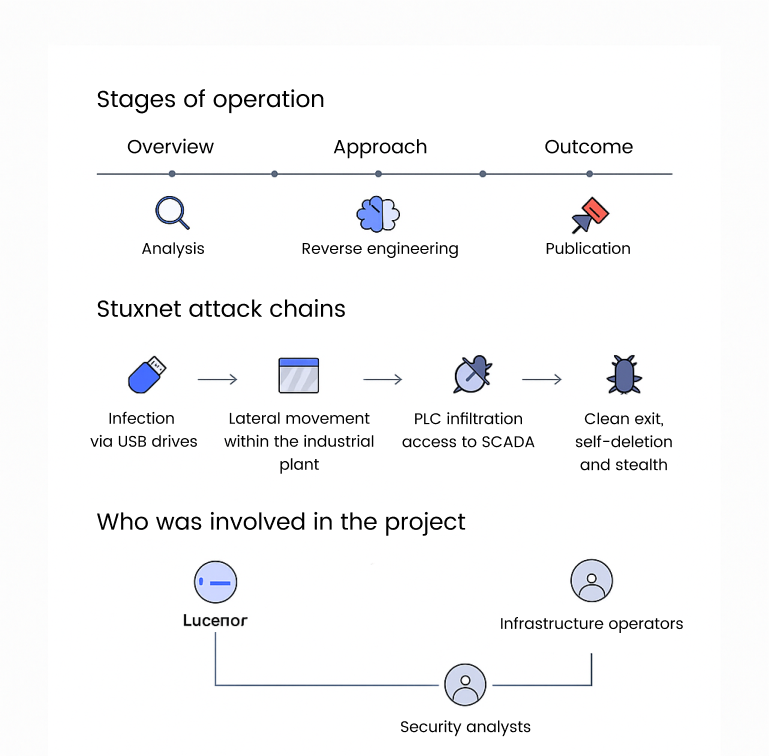
Overview
A global cybersecurity think tank sought expert assistance to analyze and document Stuxnet—the world’s first known industrial cyber weapon, engineered to target and disrupt critical industrial control systems. The project’s goal was to uncover Stuxnet’s mechanisms, assess its impact, and share actionable intelligence with the broader security community.
Approach
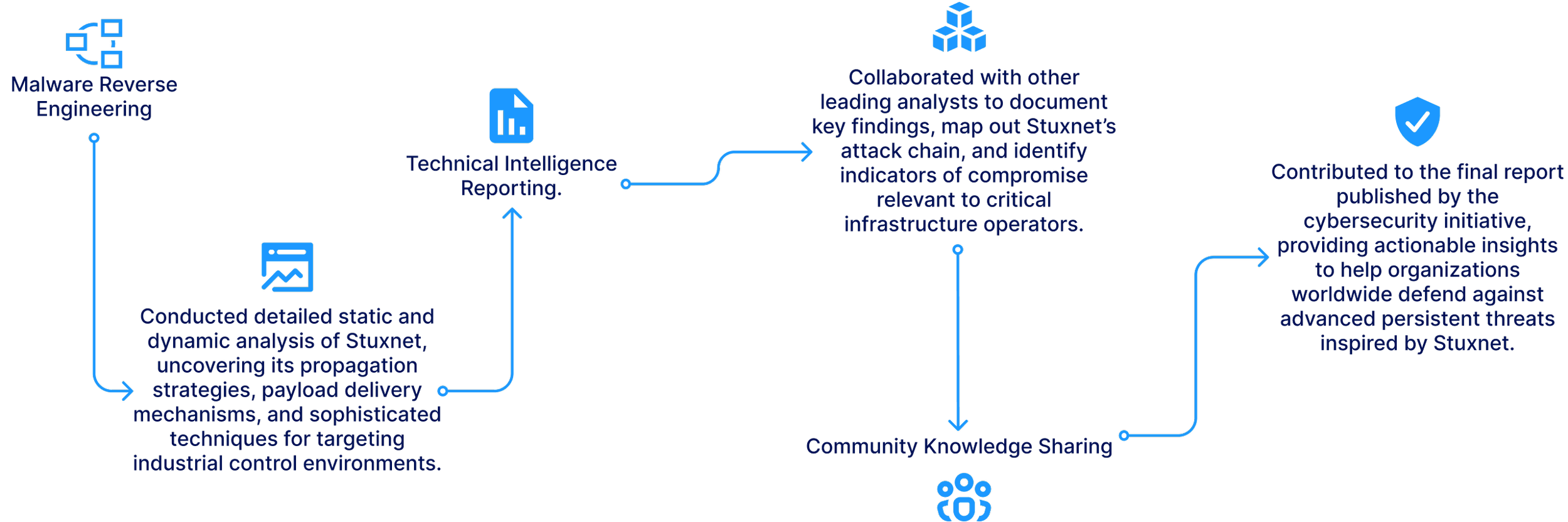
Our team of Lucenor expert consultants conducted in-depth reverse engineering and threat analysis to uncover the mechanisms of Stuxnet.
Our contributions included:
Outcome
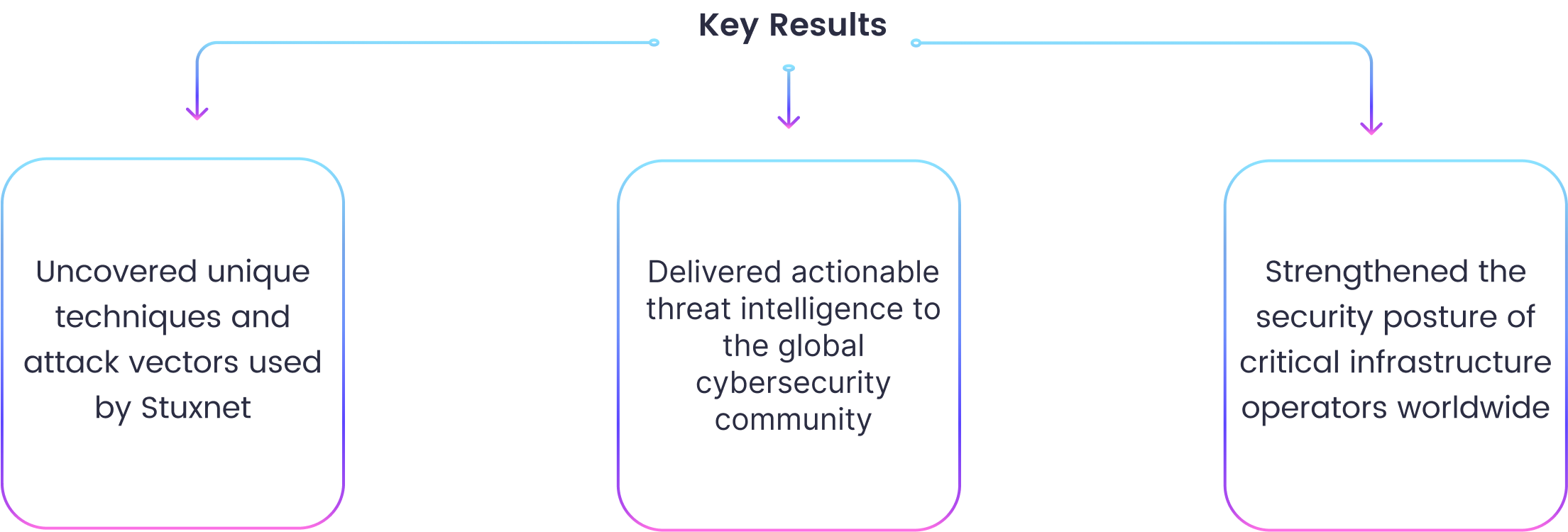
Our research findings equipped key critical infrastructure operators with the actionable intelligence and tailored insights needed to defend against the complex cyber threats exemplified by Stuxnet.
Innovative Consulting for a Connected World
Let’s start a conversation. Our team is here to provide tailored insights and secure solutions for your business needs.
Let’s talk!